Rampart
Policy engine for AI agent tool calls.
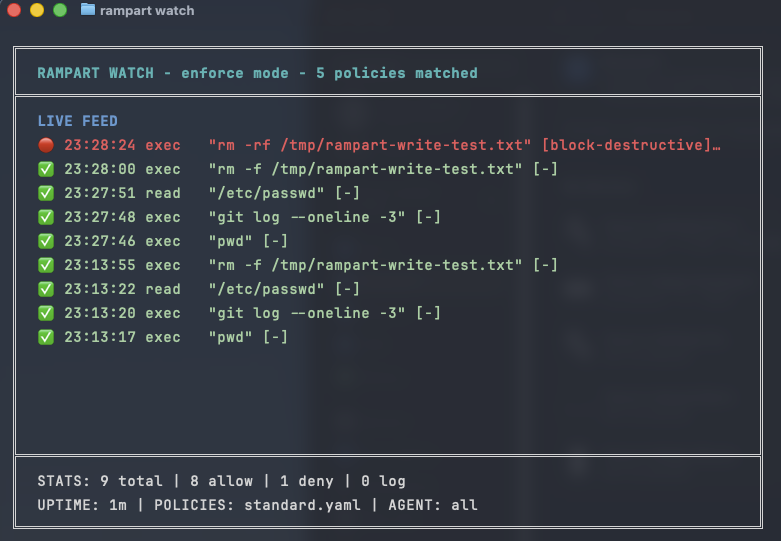
Live dashboard — green for allowed, red for denied. Every agent tool call evaluated in microseconds.
What it does
AI agents call tools — exec, read, write, fetch, MCP. Rampart sits between the agent and those calls, evaluates them against your policies, and blocks what shouldn't run.
Traditional sandboxing is all-or-nothing. Rampart gives you granular control: allow git push, deny rm -rf /, log every curl for review. Per tool, per pattern, with a hash-chained audit trail.
Install
Requires Go 1.24+.
go install github.com/peg/rampart/cmd/rampart@latestrampart is in your system PATH.Quick fix:
sudo ln -sf $(go env GOPATH)/bin/rampart /usr/local/bin/rampart
Or build from source:
git clone https://github.com/peg/rampart.git
cd rampart
go build -o rampart ./cmd/rampart
sudo mv rampart /usr/local/bin/Protect Claude Code
Native integration through Claude Code's hook system. One command:
# Install the hook
rampart setup claude-code
# Use Claude Code normally — Rampart evaluates every tool call
claude
# Open the live dashboard in another terminal
rampart watchEvery Bash command, file read, and file write goes through Rampart before execution. Blocked calls never run — Claude Code gets a policy denial and moves on.
Protect any agent
For agents that read the $SHELL environment variable (Aider, OpenCode, Continue, Cline):
rampart wrap -- aider
rampart wrap -- opencode
rampart wrap -- python my_agent.pyFor MCP servers:
# Wrap any MCP server — denied tool calls never reach it
rampart mcp -- npx @modelcontextprotocol/server-filesystem .What gets blocked
The default standard profile blocks out of the box:
| Category | Examples | Action |
|---|---|---|
| Destructive commands | rm -rf /, mkfs, dd if= |
deny |
| Credential access | ~/.ssh/id_*, ~/.aws/credentials |
deny |
| Sensitive writes | /etc/, ~/.bashrc, ~/.ssh/ |
deny |
| Exfil domains | *.ngrok.io, webhook.site |
deny |
| Privileged commands | sudo, kubectl delete |
log |
| Network commands | curl, wget, scp |
log |
| Credential leaks | AWS keys, private keys, tokens in output | deny |
| Everything else | git push, ls, go build |
allow |
Policies are YAML. Write your own or use the built-in profiles: standard, paranoid, yolo.
Details
| Language | Go — single binary, no runtime dependencies |
| Overhead | 5–50µs per policy evaluation |
| Audit | Hash-chained JSONL with tamper detection |
| Platforms | Linux, macOS (hooks + wrap). Windows (hooks only). |
| License | Apache 2.0 |